Digital banking runs on speed and trust. Customers open accounts, move money in seconds, and deposit checks from their phones, trusting that security protects them in the background.
Fraudsters exploit that trust. They automate phishing, buy stolen data, and use deepfakes to impersonate executives. In 2024, the FBI reported $16.6 billion in losses from internet crime, up 33 percent from the previous year.
The answer is not to slow transactions but to make smarter decisions at the moment they happen.
This guide explains what internet fraud prevention really means today, how online threats are evolving, and ten proven protection strategies any financial institution can put into practice right now.
Key takeaways:
- Prevention happens before the loss: Internet fraud prevention focuses on detecting intent in real time during logins, deposits, and payments rather than reacting after funds are gone.
- Fraud is evolving fast: Account takeovers, synthetic identities, and AI-powered impersonation scams are growing, outpacing legacy rule-based systems.
- Faster banking means bigger attack surfaces: Instant payments, open APIs, and frictionless onboarding create more entry points for fraud unless matched with adaptive controls.
- Smarter automation reduces strain: Real-time analytics and behavioral intelligence cut down false positives, manual reviews, and operational costs.
- VALID Systems keeps institutions ahead: VALID's AI-driven tools help financial institutions prevent internet fraud before it becomes a loss while keeping trusted customers moving freely.
What is internet fraud prevention?
Internet fraud prevention is a proactive system of controls that stops fraud before money leaves the account. It combines identity verification, behavioral analytics, machine learning, and clear policies supported by trained staff.
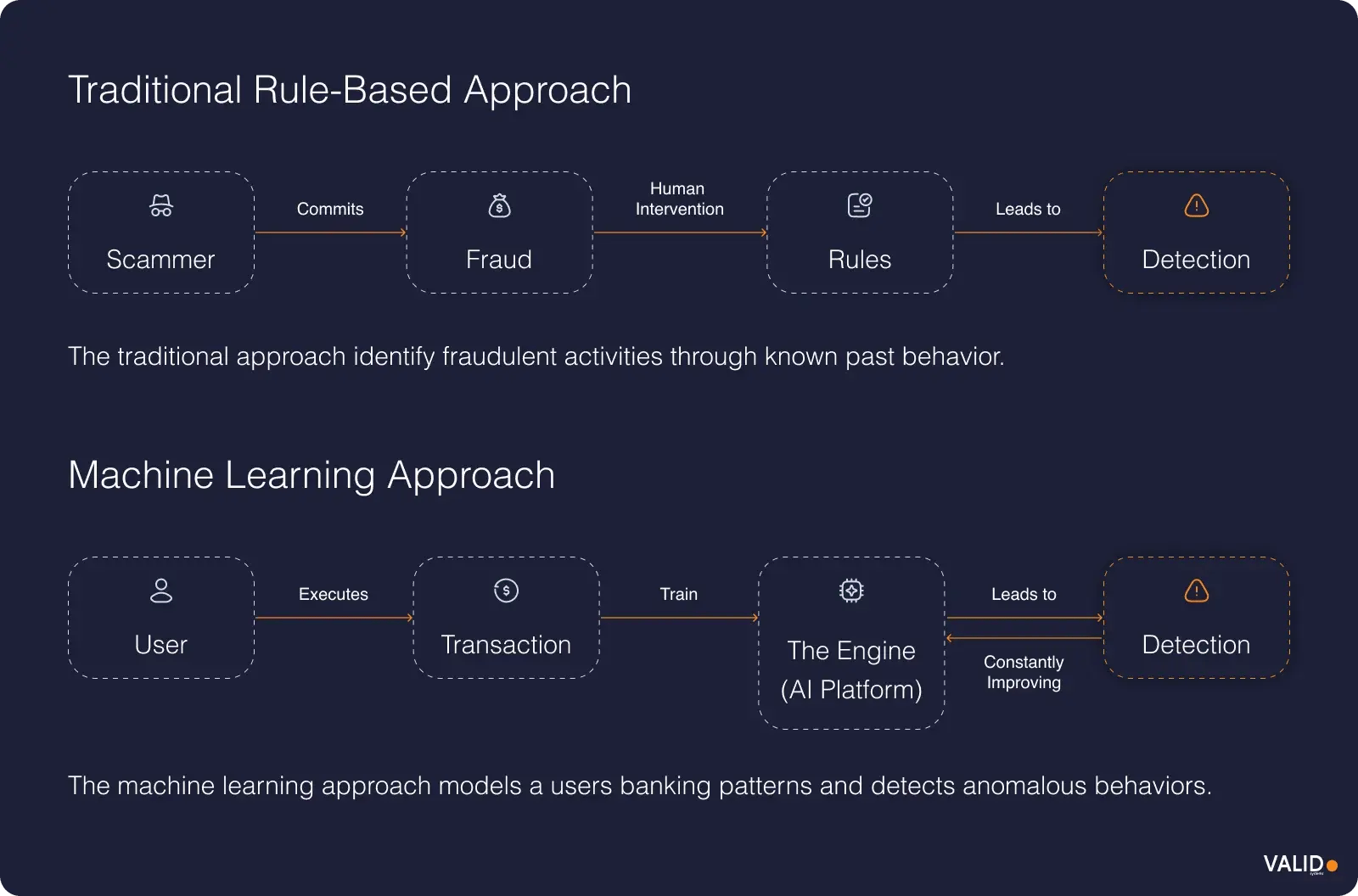
The goal is to detect intent, not just activity, across every digital channel. That includes online and mobile banking, remote deposit capture, peer-to-peer payments, open banking APIs, and embedded finance platforms.
Why prevention matters more than detection
Finding fraud after it happens means the loss is already on your books, and the customer's trust is gone. Prevention pushes decisioning to the moment it matters most –at login, at the deposit, or during a transfer. The objective is to approve legitimate transactions instantly while escalating only when risk signals appear.
Stakeholders and channels
Internet fraud touches every part of the financial ecosystem: banks, credit unions, fintechs, payment processors, lenders, and online marketplaces. Customers are often the first to feel the impact, but institutions bear the cost when fraud crosses channels.
A phishing attack that starts with a stolen login can end with a fraudulent mobile deposit or an outbound wire. Proper prevention requires correlating data across all digital touchpoints so institutions view risk as one connected picture, not a set of isolated alerts.
Evolving attack types in internet fraud
Here are the primary attack types defining internet fraud:
Account takeover (ATO)
Account Takeover (ATO) occurs when a bad actor gains access to a real account and uses it to move funds, apply for credit, or loot resources. It is surging in severity and scale.
For example, one report shows that ATO-related fraud increased by 24% year over year in 2024. A different study found that attackers targeted 99% of the monitored organizations and successfully compromised accounts in 62% of them.
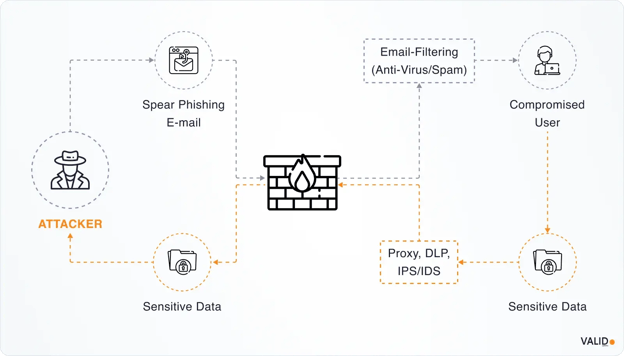
Why ATO keeps climbing:
- Massive data breaches and password reuse drive credential stuffing attacks. (In 2025, 62% of Americans admitted to reusing passwords, and 52% of login attempts involved leaked credentials.)
- SIM swaps and adversary-in-the-middle techniques to defeat MFA.
- Fraud tools and automation are lowering the marginal cost of attack.
- Institutions that lean hard on digital channels often lack a converged view of identity, behaviour, and session.
For institutions, the message is clear: treat every login, payment, deposit, and account change as compromised until you confirm it is safe.
Synthetic identity fraud
Synthetic identity fraud (SIF) involves fraudsters combining real PII (such as SSNs) with fake names, addresses, or DOBs to create a new "person" who passes basic checks. These identities can open accounts, obtain credit, launder proceeds, and often remain undetected for long periods.
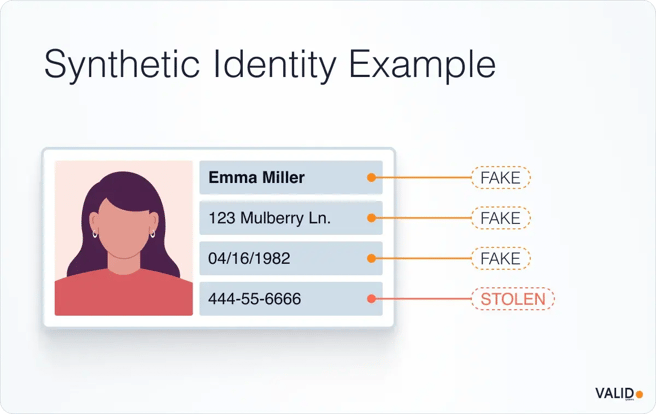
The numbers underline the severity: definitive losses are harder to pinpoint, but estimates suggest U.S. annual losses will climb to $23 billion or more by 2030. One survey found that 40% of banks believe SIF will be among their greatest threats in 2025. The same study claims that around 95% of synthetic identities go undetected during onboarding.
What this means in practice: criminals build fake identities over weeks, months, or years, layer credit and deposit activity, then trigger high-value fraud or bail out the identities once exposure is high. Many legacy systems simply aren't designed to detect that kind of "slow burn" fraud.
Deposit and check fraud (RDC/ATM/Branch)
Even as digital channels dominate, checks and deposits remain a key vector for fraud. Fraud schemes via Remote Deposit Capture (RDC), ATMs, and branch deposits exploit speed, weak verification, and cross-account networks.
These schemes often combine fake or altered checks, duplicate submissions, mule networks, and cross-account movement that exploit the availability of clear funds and the complexity of multi-channel flows.
Phishing, brand impersonation, and AI-augmented attacks
Fraudsters are now leaning into AI, deepfakes, voice clones, and realistic impersonation of trusted brands, executives, or family members.

One study found that more than one-third (35%) of UK businesses reported being targeted by AI-related fraud in early 2025, up from 23% last year. AI tools make it cheaper and faster to generate convincing video or audio that bypasses human checks or trick staff into authorising wire transfers or account changes.
Other trends include "pig-butchering" romance scams, QR-code phishing ("quishing"), and deepfake-enabled CEO-fraud campaigns.
Why internet fraud keeps getting worse
Financial technology keeps removing friction, but every shortcut creates a new opening for abuse. Modern banking moves faster than ever, and fraudsters have learned to exploit that speed.
The key drivers behind today's surge in internet fraud include:
- Frictionless onboarding and instant money movement that let bad actors act before risk systems respond.
- Fraud-as-a-Service (FaaS) platforms that sell ready-made attack kits, botnets, and deepfake tools to anyone willing to pay.
- Open APIs and third-party integrations that expand the number of entry points criminals can target.
- Remote and digital-first banking habits that grew after the pandemic, while many institutions still rely on outdated controls.
Each of these factors compounds the others. As convenience grows, so does exposure, and the gap between innovation and protection continues to widen.
The business impact of modern internet fraud
The cost of internet fraud is rising at a record pace.
In 2024, U.S. consumers reported $12.5 billion in fraud losses, a 25% increase from the previous year, according to the Federal Trade Commission. Every incident carries hidden expenses: charge-offs, reimbursements, investigation time, and lost customer confidence.
Fraud also creates operational strain:
- Manual review queues grow longer,
- False positives frustrate genuine customers,
- Teams waste hours chasing low-risk alerts.
When fraud does slip through, the reputational damage and regulatory pressure can be even more expensive than the initial loss.
The takeaway is simple: the same innovations that make digital banking faster also make it riskier. Institutions that invest in real-time, data-driven fraud prevention maintain their growth, reputation, and customer base.
10 ways of protection for internet fraud prevention
The next generation of defense relies on adaptive analytics, behavioral intelligence, and network collaboration.
The following ten steps outline how leading banks and fintechs are turning these principles into daily practice:
1. Move from static rules to adaptive, real-time scoring
Timely decisions reduce exposure. Over 50% of fraud losses come from events where detection was too slow or only after the fact. Real-time scoring shifts you toward pre-emptive control.
Design your system so that every customer event – login, new account creation, mobile deposit, payment initiation – is immediately scored for risk using device attributes, IP geolocation, session behavior, account history, peer-network graphs, and known fraud indicators.
Operational steps:
- Map all "edges" where customers interact (web/app/ATM/branch) and enable risk-scoring at each.
- Build or integrate a scoring engine that ingests device fingerprinting, previously flagged networks, velocity features, and account relationships.
- Auto-approve transactions below a low-risk threshold; auto-escalate those above a high threshold; route those in between for review.
- Monitor false-positive rate monthly and adjust score thresholds accordingly.
Pro Tip:
VALID’s CheckDetect enables banks to implement real-time risk scoring by analyzing behavioral, historical, and contextual data at the moment of transaction. This dynamic approach replaces static rules, allowing faster, more accurate decisions before funds are released.
2. Operationalize behavioral analytics across channels
Anomalous behaviour often signals fraud.
Construct behavioural profiles for each account or user that capture typical deposit amounts, payer/payee patterns, login times, device usage, and geography. Feed deviations into your model.
Operational steps:
- Use historical data to build baseline metrics (e.g., average monthly deposit, typical login hours, common payees).
- Define anomaly triggers (e.g., deposit amount > 95th percentile, login from unusual location, new device + large transfer).
- Integrate these triggers into your scoring engine.
- Review captured anomalies weekly and adjust thresholds or add features as needed.
- Share anomaly findings with your fraud analytics/data science teams for refinement.
Pro tip:
VALID’s Consortium Network gives banks access to shared behavioral data and fraud indicators from across institutions. Using these insights helps benchmark activity against broader patterns, improving anomaly detection accuracy and reducing false positives across channels.
3. Integrate device and session intelligence
Fraudsters exploit boundaries. A login via mobile, followed by a deposit via ATM, and a payout via web may look like three separate events, but the pattern tells a story only when correlated.
Link sessions, devices, accounts, payees, and payment rails across channels (mobile, web, ATM, branch). Build graph-based views of relationships and flow patterns.
Operational steps:
- Build "entity resolution" logic: device ↔ account ↔ payee.
- Ingest logs from all channels into a unified analytics hub.
- Use graph analytics (e.g., "one device → many accounts → many payees") to surface mule networks, collusion, or repeat patterns.
- Set alerts for patterns such as multiple depositors into a single account, the same payee receiving from multiple accounts, and device access across high-risk channels.
- Rotate model features quarterly to include new link types (API calls, new payee patterns, vendor changes).
4. Modernize authentication with context-based verification
While credentials are swappable, devices often persist. Shared infrastructure across attacks allows earlier detection.
Capture device specifics (OS version, emulator/sandbox indicators, potential root/jailbreak, automation signatures), session behaviour (mouse/touch dynamics, speed of input, repeated failures), and flagged infrastructure (proxy/VPN).
Operational steps:
- Implement device-fingerprinting services or SDKs for apps/web.
- Tag devices with a risk score component (for example: rooted → +15 risk points, emulator → +10).
- Combine device risk with session and behavioural features in your scoring model.
- Monitor devices that repeatedly appear in flagged or declined events and auto-escalate or block.
- Update the device risk taxonomy semi-annually with intelligence from threat feeds.
5. Strengthen velocity and transaction-limit controls
Implement authentication that scales with risk. Low-risk sessions proceed without intervention; high-risk sessions trigger step-up verification (biometrics, passkeys, callback, secondary device).
Focused step-up preserves user experience while protecting high-value flows.
Operational steps:
- Define risk thresholds for authentication interventions (e.g., login from a new device in a high-risk geography + a large payout).
- Enable modern authentication options for high-risk actions.
- Monitor authentication success/failure rates and user drop-off metrics to balance UX and security.
- Train frontline staff in escalation protocols and end-user communications for step-up scenarios.
6. Detect and contain social-engineering and deepfake threats
Establish per-channel velocity thresholds (e.g., deposits per hour/day, new payees per account, transfers per day) paired with dynamic holds driven by risk score and account history.
Operational steps:
- Define baseline velocity thresholds for each product and channel.
- Create dynamic hold logic: if risk score > X, hold deposit for Y hours; if risk score < Z and history is clean, approve instantly.
- Track hold outcomes: conversion to fraud vs clean release. Adjust logic weekly.
- Report hold-release ratios and manual review volumes to senior management monthly.
7. Leverage consortium and third-party intelligence
Focus on the human component. Define high-risk flows and insert human verification or callback. Train staff and customers on emerging social engineering threats, especially those driven by generative AI.
Operational steps:
- Identify and document high-risk flows requiring human review or secondary validation.
- Create standard scripts for callback verification or video verification of large transactions.
- Train fraud teams quarterly on the latest social-engineering tactics.
- Include customer education campaigns (e.g., on voice-clone impersonation) as part of your prevention strategy.
8. Automate exception triage and feedback loops
Fraud rings don't respect institutional boundaries. Join or build networks that share anonymised fraud signals across institutions (device clusters, mule accounts, IP groups, compromised credentials). Integrate those signals into your scoring engine.
Operational steps:
- Evaluate and join a reputable fraud-intelligence consortium.
- Feed external signals into your scoring engine with equal weight to internal signals (after proper validation).
- Assign dedicated resources to review external alerts and determine applicability to your portfolio.
- Develop SLA for ingestion of new intelligence (e.g., 24-hour maximum latency).
9. Balance good-funds availability with risk exposure
Manual review is expensive and slow. Therefore, automate review routing so only ambiguous or high-risk events reach human analysts.
Provide review dashboards with full context (device/session graphs, anomaly data, peer-network flags), and use review outcomes to retrain models.
Operational steps:
- Build review workflow: auto-clear low-risk, auto-hold/decline high-risk, route mid-risk to analysts.
- Provide analysts with a ranked risk breakdown, evidence links, and a history of previous activity.
- Set metrics: review volume, average time per review, analyst override rate, false-positive/false-negative ratio.
- Use review outcomes weekly to retrain scoring models and refine workflow rules.
10. Modernise deposit-fraud and good-funds decisioning
Score deposit items (mobile, branch, ATM) before funds are available. Create dynamic availability windows based on risk and monitor money movement patterns such as redeposit, layering, and rapid payouts.
Operational steps:
- Score each deposit item in real time using deposit metadata (amount, deposit channel, account history, issuer history, payee network).
- Monitor patterns of rapid redeposit or payout and link to the original deposit item through graph analytics.
- Report on deposit fraud loss trends quarterly and proactively adjust hold-logic thresholds.
VALID Systems' internet fraud prevention
The institutions winning today are those that treat prevention as a core part of daily operations, not as a separate function. By combining real-time scoring, behavioral intelligence, and cross-channel visibility, financial institutions can turn fraud from an unpredictable threat into a controlled risk.
VALID Systems delivers the intelligence and infrastructure to make that shift possible. This solutions help banks, credit unions, and fintechs protect customers, accelerate transactions, and strengthen their balance sheets simultaneously.
VALID Systems transforms internet fraud prevention through:
- Adaptive AI-powered scoring: CheckDetect applies behavioral analytics and device intelligence to every deposit, transaction, and session in real time. The platform identifies more than 75 percent of potential charge-offs before funds move, allowing institutions to act before losses occur.
- Instant funds with controlled exposure: InteliFUNDS delivers same-day funding while maintaining safety and compliance. By combining real-time scoring with dynamic decisioning, institutions can offer instant access without increasing risk or charge-offs.
- Network-level intelligence: With visibility into more than 450 million accounts and $4 trillion in annual transactions, Edge Data Consortium gives institutions a collective advantage.
Fraud risk management today is about timing. The goal is to act before losses hit the books. VALID Systems gives institutions the capability to detect, decide, and prevent fraud in real time while keeping good customers moving freely.
Make internet fraud prevention proactive, not reactive.
Learn how VALID Systems helps financial institutions stop internet fraud before it starts and turn risk control into measurable performance.
