It rarely starts with a dramatic theft. More often, it's a small charge you don't remember. You ignore it, thinking it's nothing, until a few more appear. Suddenly, your card is frozen, your account is under review, and that small oversight turns into a weekend spent disputing charges and resetting passwords.
While these incidents often begin quietly, their reach extends deep into the financial ecosystem, affecting consumers, issuers, and payment networks alike.
This guide will help you fight back. We'll explain the most common forms of credit card fraud, your legal protections, early warning signs, and practical steps to secure your accounts.
Key takeaways:
- Credit card fraud takes many forms: It's no longer limited to stolen cards. Fraud today includes synthetic identities, social engineering, SIM swaps, and account takeovers.
- Recognizing early red flags is critical: Fraud often begins quietly with small or unfamiliar charges, sudden changes in contact information, or repeated declines.
- Financial institutions need adaptive, data-driven detection: Static rules and manual reviews are falling behind. Real-time analytics and behavioral modeling now form the foundation of effective credit card fraud prevention.
- VALID helps institutions move from reaction to prevention: VALID Systems supports banks with intelligent, real-time fraud detection technology that identifies high-risk transactions before funds move.
What is credit card fraud?
Credit card fraud represents one of the most persistent and costly forms of payment crime in the How to Prevent and Protect Yourself from Credit Card FraudU.S. financial system. In regulatory terms, it occurs when an unauthorized party uses a customer's card or card credentials to initiate transactions or access an account, resulting in financial loss to the issuer, the cardholder, or both (OCC).
Credit cards may feel secure, but fraud is climbing fast. The FTC's 2024 Consumer Sentinel Network Data Book recorded 449,032 cases of credit-card identity theft, up again from the previous year.
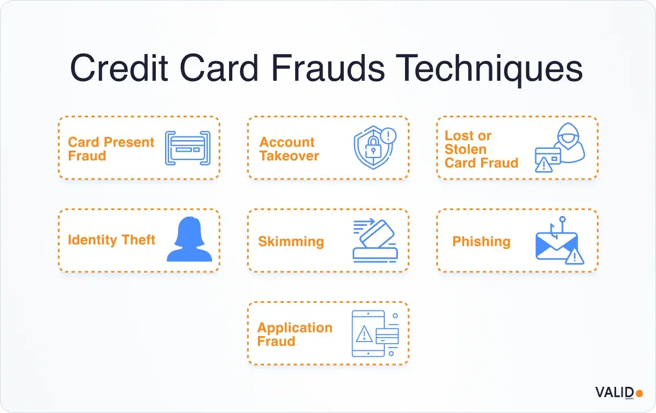
For financial institutions, credit card fraud extends far beyond stolen cards. It spans a wide set of vectors:
- Card theft and counterfeit use: Physical cards stolen or duplicated using compromised point-of-sale terminals and ATM skimmers.
- Account takeover (ATO): Criminals use phishing or credential-stuffing attacks to gain control of online or mobile banking accounts, update contact details, and order replacement cards.
- Card-not-present (CNP) fraud: Theft of primary account numbers, CVVs, and expiry dates for use in e-commerce or remote transactions (OCC).
- Mail interception and reissuance abuse: Fraudsters divert legitimate cards during delivery or manipulate change-of-address requests to intercept them.
- Social engineering and impostor scams: Attackers impersonate trusted entities such as bank staff or government officials to solicit credentials or one-time passcodes.
- Mobile and SIM-swap exploitation: Control of a customer's phone number allows interception of authentication codes and account resets.
Often, identity theft and credit card fraud overlap. For example, a criminal who steals your Social Security number might open a new credit card in your name, then run up charges (a form of "credit card identity theft").
Common red flags indicating credit card fraud
Early identification of fraudulent behavior is critical for minimizing both customer impact and institutional exposure. While methods evolve, several recurring red flags consistently indicate potential credit card or identity misuse:
1. Unusual transaction patterns
Fraud often starts small. Criminals may run low-value "test" charges, typically under $5, to confirm stolen card details are active before executing larger purchases.
Example: A burst of $1–$3 transactions across multiple e-commerce sites in a short period can indicate automated credential testing.
2. Account information changes
Unauthorized updates to email addresses, phone numbers, or mailing information are common precursors to account takeover. Fraudsters frequently alter credentials just before requesting new cards or resetting passwords, effectively locking legitimate users out.
Example: A customer's profile email is changed at 2 a.m., followed by a card reissue request within the same hour, a pattern strongly correlated with ATO attempts.
3. Multiple declines or authorization attempts
Repeated declined transactions across multiple merchants or locations can indicate credential stuffing or synthetic identity testing. These attempts often occur in rapid succession, sometimes using slightly altered card data.
4. Out-of-profile spending behavior
Sudden changes in merchant category, location, or purchase volume can signal compromised accounts. Behavioral deviation is one of the earliest measurable indicators of fraud.
Example: A customer with a long history of small domestic retail transactions suddenly initiates several high-ticket cross-border purchases within minutes.
5. Unexpected account openings
When a credit card or line of credit appears under a customer's name without their knowledge, identity theft is likely involved.
Fraudsters use stolen personal data, or synthetic combinations of real and fabricated information, to establish new credit profiles.
6. Compromised communication channels
Returned mail, undelivered cards, or missing account statements may point to mail interception or address manipulation.
Example: A customer reports not receiving a reissued card, only for transaction data to show activation and usage within days of shipment.
7. Customer-reported alerts
Customer complaints about unrecognized charges, blocked logins, or sudden account locks often precede internal fraud detection triggers. These firsthand reports can provide valuable early warning when analyzed collectively.
Regulatory landscape and compliance expectations
The regulatory framework governing card fraud in the U.S. continues to evolve, emphasizing operational resilience, identity assurance, and cross-channel oversight:
- OCC (Office of the Comptroller of the Currency): Focuses on strengthening card-risk governance and aligning fraud prevention with enterprise-wide risk management. Banks document fraud-risk assessments, oversee third-party vendors directly, and ensure their fraud-detection and recovery processes remain continuous and resilient.
- FFIEC (Federal Financial Institutions Examination Council): Reinforces strong authentication and access management through its 2024 guidance. Institutions must apply multi-factor and adaptive authentication, monitor behavioral and device-based anomalies, and maintain layered security across card, online, and mobile channels.
- CFPB (Consumer Financial Protection Bureau): Enforces consumer protection standards under Regulation Z and UDAAP. It penalizes delayed reimbursements, poor fraud investigation practices, and inconsistent application of zero-liability rules.
- FinCEN (Financial Crimes Enforcement Network): Expands synthetic identity and AML reporting expectations for 2024–2025. Institutions must identify and report synthetic-account activity through updated SAR categories and integrate fraud and AML data streams to detect cross-channel typologies spanning cards, ACH, and wires.
Emerging credit check fraud vectors
The latest fraud trends in 2025 show that attacks are becoming faster, smarter, and harder to trace. Criminals now use advanced technology and data manipulation to exploit every point of contact between banks and customers.
For financial institutions, the biggest shift is that fraud is no longer about isolated transactions but about manipulating entire verification systems:
Deepfake voice and video impersonation
Generative AI has turned voice and video cloning into one of the most alarming threats in banking. Fraudsters now mimic executives, account holders, and call-center agents to authorize payments or access sensitive data.
The next wave of these attacks includes real-time video forgeries that can trick even advanced "liveness" checks during identity verification.
AI-enhanced synthetic identities
Synthetic identity fraud has entered a new phase where artificial intelligence helps create convincing documents, pay stubs, and ID photos. These fake profiles pass standard onboarding procedures and remain undetected until losses surface months later.
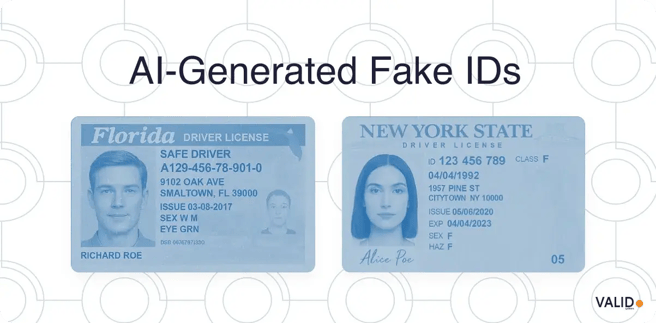
The Federal Reserve and FinCEN both identify synthetic identities as one of the fastest-growing sources of credit and card-related losses in the U.S.
Cross-channel fraud and money movement
Card fraud is increasingly connected to other financial crimes. Stolen funds move quickly across cards, peer-to-peer payment apps, and ACH transfers, making them difficult to trace.
Organized groups coordinate "mule" accounts to launder proceeds across different payment systems within hours. This cross-channel convergence now represents one of the most complex challenges for banks and payment providers.
Compromise of biometric and mobile authentication
As mobile banking expands, so does the risk of compromised devices. Fraudsters use stolen biometric data, replay attacks, and SIM swaps to take over accounts and intercept one-time codes.
Fraudsters increasingly use spoofed fingerprints, facial scans, and voice recordings captured online to defeat authentication barriers once considered secure.
6 steps to modernize credit card fraud detection and response
The next generation of defense combines three capabilities: adaptive analytics, collective intelligence, and continuous behavioral feedback. Here's how leading institutions are putting that into practice:
1. Transition from static rules to adaptive intelligence
Rules alone cannot keep pace with dynamic fraud patterns. Each new scheme quickly renders static thresholds obsolete.
Operational shift:
- Deploy AI-driven risk models that score transactions continuously, not just at point-of-sale or login.
- Move from "binary approval/decline" to tiered decisioning, where the system automatically escalates gray-zone cases for step-up verification.
- Blend supervised learning (confirmed fraud data) with unsupervised pattern recognition to detect emerging typologies.
- Recalibrate detection thresholds weekly or daily as new data feeds become available.
2. Operationalize consortium intelligence
Fraud rings no longer target one bank at a time. They move laterally across institutions, exploiting delays in intelligence sharing. Consortium collaboration converts isolated detection into networked defense.
Steps to implement:
- Participate in industry data-sharing frameworks that exchange anonymized fraud signals (device IDs, mule accounts, IP clusters).
- Integrate consortium alerts into internal scoring pipelines so cross-bank activity raises automated risk levels.
- Assign dedicated analysts to validate and contribute consortium intelligence, ensuring two-way benefit.
- Use shared data to strengthen model training. Every confirmed case from the network enhances your predictive accuracy.
3. Integrate behavioral analytics across payment channels
Fraud is rarely tied to a single product. A mule deposit, an ACH withdrawal, and a fraudulent card purchase often occur within hours of each other. The ability to connect these signals in real time defines modern risk intelligence.
Actionable priorities:
- Unify transaction monitoring across all payment rails (check, card, ACH, wire, and P2P).
- Create a customer-level behavioral profile that evolves with every interaction, not a static score.
- Flag behavioral inconsistencies such as normal logins paired with high-velocity outbound payments.
- Automate cross-channel linkage so alerts from one product dynamically adjust risk ratings in others.
4. Establish continuous learning and feedback loops
Fraud models degrade quickly without active learning. Continuous improvement must be built into your operational rhythm, not treated as an annual update.
Key practices:
- Automate feedback from case investigators directly into your model-training pipeline.
- Use closed-loop analytics: confirmed fraud retrains the model within hours.
- Schedule frequent red-team exercises to simulate adversarial behavior and test model resilience.
- Create joint task forces among fraud, AML, and data science teams to jointly interpret new typologies.
5. Align Fraud and AML Intelligence
Fraudsters use multiple channels to move and legitimize stolen funds. The separation between fraud and AML functions often delays detection. Integrating both perspectives provides the complete picture of financial crime.
Implementation guidance:
- Merge transaction monitoring outputs from fraud and AML systems into a unified intelligence hub.
- Tag transactions that display both fraud and AML risk signals (velocity anomalies, structuring behavior, or mule activity).
- Correlate SAR filings with upstream fraud alerts to identify repeat entities or networks.
- Train investigators on dual-analysis frameworks that consider both fraud exposure and laundering risk.
6. Build predictive collaboration across the ecosystem
Fraud prevention is a shared infrastructure challenge. The future belongs to institutions that collaborate, not isolate.
Strategic moves:
- Create internal "fusion centers" where fraud, compliance, and cybersecurity teams analyze intelligence together.
- Engage with law enforcement and industry consortiums to exchange pattern-level data, not just incident reports.
- Support open-standard APIs that let banks feed and receive verified risk intelligence in real time.
How VALID Systems strengthens check fraud defenses
VALID Systems does not provide card solutions. However, its advanced check and deposit fraud analytics play a crucial role in protecting financial institutions from the kinds of losses that often begin with compromised accounts and end up impacting debit or card-linked activity.
By analyzing behavioral patterns, account activity, and cross-channel data in real time, VALID enables financial institutions to detect anomalies early and take immediate action. This proactive approach helps prevent account takeovers and reduces downstream exposure in related payment channels.
With VALID, banks gain faster detection, fewer false positives, and stronger overall fraud resilience.
Ready to stay ahead of check card fraud?
Book a free consultation with VALID Systems to see how our AI-driven solutions can help your institution detect and prevent check card fraud in real time.
