Wire fraud drains accounts in seconds, often beyond recovery. Check fraud inflicts steady losses through stolen mail, altered payees, and counterfeit items.
Wire fraud vs check fraud? They both remain rising fraud categories.
In 2024, the FBI reported $12.5 billion in wire fraud losses, while the ABA estimates that check fraud losses exceeded $24 billion that same year, with nearly one-third of these attempts resulting in actual losses.
In this guide, we'll break down the mechanics of each scheme, examine liability under UCC and regulatory guidance, highlight recent case examples, and outline proven controls.
The goal is simple: help banks shrink the loss curve without slowing down customer payments.
Key takeaways:
- Wire fraud moves fast: Wire transfers settle almost instantly, making it very difficult to reverse fraudulent payments. Business Email Compromise (BEC) remains one of the most common ways attackers initiate fraudulent wire transfers.
- Check fraud is still a major threat: Even with digital payments on the rise, criminals continue to exploit stolen mail, altered payees, and counterfeit checks, making it a persistent risk for banks and businesses.
- Both payment rails share vulnerabilities: Fraudsters target wires and checks because both are widely used and trusted. Wires offer speed and large amounts in one hit, while checks provide volume and accessibility.
- Strong controls are critical: Banks need layered defenses such as out-of-band verification, dual control, Positive Pay, image forensics, and dynamic holds to reduce losses without slowing down customers.
- VALID Systems helps banks combat both threats: VALID provides real-time scoring for check deposits and continuous monitoring for wire transfers.
Wire fraud vs check fraud: which is riskier today?
There's no simple answer. Both are rising threats, and both exploit weak points in payment systems that banks and businesses rely on every day. Wire fraud concentrates losses in a few devastating events, while check fraud spreads them across thousands of items.
The only way to answer which is riskier is to examine each one in detail, looking at the mechanics, liability, and controls before comparing them side by side.
What is wire fraud?
Wire fraud is a federal crime under 18 U.S.C. § 1343. It occurs when someone devises a scheme to defraud or obtain money or property by false pretenses and uses wire, radio, or television communications in interstate or foreign commerce in furtherance of that scheme.
If the wire fraud scheme affects a financial institution or involves disaster relief, the penalties are harsher: a fine of up to $1,000,000, up to 30 years in prison, or both. Otherwise, basic offenses under the statute carry a sentencing of up to 20 years in prison.
How it happens
Wire fraud typically unfolds in several stages:
- Reconnaissance and targeting: Fraudsters begin by identifying who controls the money. They study accounts payable teams, payroll staff, or executives, pulling details from company websites, social media, and even prior email leaks to set up convincing scenarios.
- Initial compromise: Criminals gain access through phishing emails, stolen credentials, or malware infections. In other cases, criminals register domains that closely resemble those of legitimate vendors or partners.
- Business Email Compromise (BEC): Attackers pose as trusted contacts. They slip into conversations or send look-alike emails, using fake invoices, payroll diversions, or executive "urgent requests" to push payment changes.
- Fraudulent instructions: Once in position, they send new payment directions marked as 'urgent' or 'confidential'. The goal is to rush staff into bypassing regular checks and authorizing the transfer.
- Execution of the transfer: Fraudsters move funds through Fedwire, SWIFT, or other rails. They often move the money through several domestic accounts before sending it abroad, making it difficult to trace.
- Settlement and finality: The Federal Reserve or a correspondent bank completes the wire by crediting the recipient's institution, and no one can reverse the transfer.
Why it's costly
Wire fraud remains one of the most damaging crimes in banking because of how it combines speed, scale, and permanence:
- Speed and finality: Wire payments settle almost instantly across clearing rails. Once the receiving bank is credited, the transfer is final.
- High-dollar impact: Business Email Compromise (BEC), the leading driver of fraudulent wire transfers, accounted for $2.77 billion in losses, making it one of the most costly fraud categories tracked by the FBI. In January 2025, the average BEC wire request reached $24,586, up 46% from $16,799 in December 2024.
- Escrow and real estate exposure: A 2025 survey of title and escrow companies found that the share of firms reporting losses exceeding $50,000 from wire fraud rose by 31 percent, underscoring the sector's heightened vulnerability.
- Recovery is limited: In 2024, the FBI's Recovery Asset Team froze over $561 million in fraudulently obtained funds, a notable achievement, but still only a fraction of the total losses reported that year.
What is check fraud?
Check fraud exploits negotiable instruments governed by UCC Article 3 (negotiability) and UCC Article 4 (bank collections), as well as Regulation CC, which establishes rules on funds availability and return deadlines.
In practice, criminals counterfeit checks, alter payees or amounts, forge endorsements, or abuse in-clearing processes on legitimate accounts.
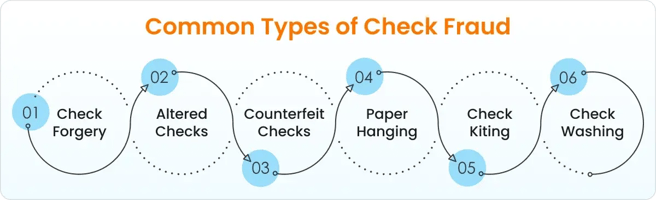
Federal prosecutors charge check fraud under several statutes, including:
- Bank fraud (18 U.S.C. § 1344): Up to 30 years in prison and fines up to $1,000,000 when a financial institution is affected.
- Mail theft (18 U.S.C. § 1708): Up to 5 years in prison and fines for stealing or possessing stolen mail, including checks.
- Forgery and counterfeiting (18 U.S.C. § 513): Up to 10 years in prison and fines for making, uttering, or possessing counterfeit or forged checks.
How it happens
Check fraud typically follows a repeatable cycle that exploits both the mail stream and bank processing rules:
- Mail theft and targeting: Criminals steal checks directly from USPS blue collection boxes, residential mailboxes, or postal distribution facilities. Many buy stolen USPS "arrow keys" on the dark web to unlock mailboxes at scale.
- Check washing and alteration: Stolen checks are chemically "washed" to remove ink, then rewritten with new payee names or higher amounts. Others are digitally scanned and reproduced as counterfeit checks.
- Forged endorsements: Fraudsters forge payee signatures or create fake IDs to deposit stolen or altered checks into mule accounts.
- In-clearing manipulation: Some schemes involve altering legitimate checks in transit through the clearing system, changing amounts or account numbers before settlement.
- Deposit methods: Altered or counterfeit checks are deposited via mobile apps, ATMs, or in person at branches, using automated systems that expedite funds availability.
- Return window exploitation: Because Regulation CC requires banks to return unpaid checks within two business days (and Treasury checks even faster), criminals exploit this tight detection window to withdraw funds before fraud teams can react.
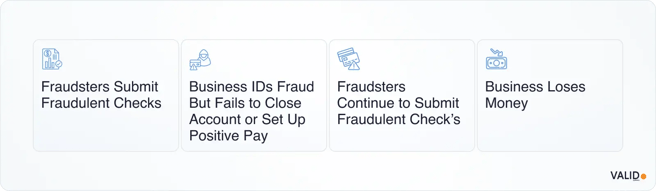
Why it's costly
Check fraud continues to strain U.S. banks and credit unions because of its scale, persistence, and reliance on systemic weaknesses:
- High volume of cases: Financial institutions filed 682,276 Suspicious Activity Reports (SARs) tied to check fraud in 2024, a level nearly identical to the 2022 peak.
- Persistent financial losses: Industry analysts estimate that total attempted check fraud exceeded $24 billion in 2024, with roughly one-third of attempts resulting in direct losses for banks.
- Organized fraud rings: Criminal networks deposit stolen or altered checks through mule accounts on a large scale, making recovery difficult and multiplying losses across multiple institutions.
Why do criminals target both check and wire payments?
Criminals continue to exploit both rails because they combine scale, accessibility, and weaknesses that are difficult for banks to seal off fully:
- Shared vulnerabilities: Both wires and checks are trusted payment methods embedded in everyday business and government transactions. Fraudsters exploit the speed of wires and the continued reliance on checks, knowing that controls lag behind criminal innovation.
- High value potential: Wires allow large-dollar thefts in a single move, while checks provide high-volume opportunities across thousands of deposits. Together, they provide criminals with two distinct yet highly profitable methods to extract funds.
- Ease of exploitation: Social engineering drives wire fraud, while mail theft and counterfeiting drive check fraud. Both attack methods are low-cost for criminals compared to the potential payout.
- Hybrid schemes: Stolen checks often provide account and routing data that fraudsters recycle into wire scams. Fraudsters fund mule accounts with altered checks and later use them to receive fraudulent wire transfers, creating a feedback loop between the two types of fraud.
How to prevent wire fraud
The following strategies can help banks and businesses reduce wire fraud losses and protect customer confidence:
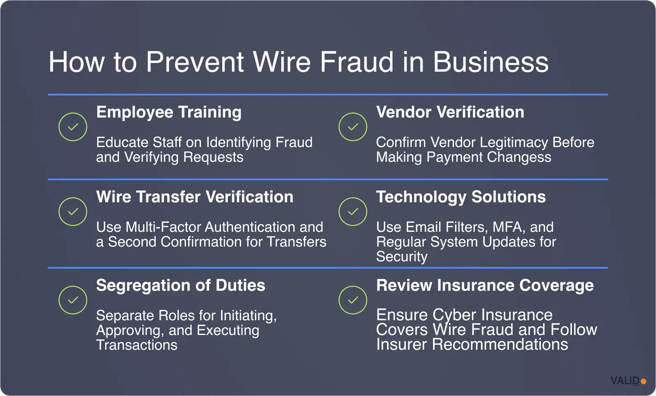
1. Verify instructions out of band
Many wire fraud cases succeed because staff rely on email alone to confirm payment details. Out-of-band verification introduces a critical layer of defense.
Steps to apply out-of-band verification:
- Call a verified number stored in your system of record whenever you receive new or changed wire instructions.
- Require callbacks for all high-value wires, even if the beneficiary has an established history of responsible behavior.
- Document every verification attempt in your workflow system for accountability and audit purposes.
Suggestion: Never confirm payment instructions using the same channel they arrived in, such as email, text, or chat. Always validate through an independent, trusted channel.
2. Enforce dual control and segregation of duties
Allowing a single employee to both initiate and release a wire transfer creates unnecessary risk. Dual control ensures that there is no single point of failure.
Steps to apply dual control:
- Require at least two unique logins for initiation and final approval.
- Segregate responsibilities across different departments or seniority levels for higher-value transfers.
- Introduce step-up authentication methods, such as tokens, biometrics, or push approvals, for the release stage.
3. Flag high-risk transactions for review
Not all wires carry the same level of risk. Some transactions warrant an immediate pause for closer inspection.
What to flag:
- Payments to first-time beneficiaries or to accounts in new payment corridors.
- Large-value transfers that exceed your institution's established thresholds.
- Transactions submitted outside of normal business hours or in unusual time zones.
4. Train staff on BEC red flags
Business Email Compromise (BEC) is one of the most common entry points for fraudulent wires. Managers must train employees to recognize the signs before approving transactions.
Red flags to teach:
- Email domains that look similar to legitimate ones (e.g., "rn" substituted for "m").
- Messages that use urgency to bypass normal approval steps.
- Requests to change bank account details unexpectedly.
Tip: Run live phishing and BEC simulations at least twice a year.
5. Build a rapid-response playbook
Even with strong controls, some fraudulent wires will get through. Having a clear playbook in place makes the difference between partial recovery and permanent loss.
Steps for rapid response:
- Contact your bank's fraud desk or wire operations team immediately to attempt a recall or hold on the transaction.
- File a complaint with the FBI's IC3 portal within hours of discovery.
- Escalate confirmed fraud cases to the FBI's Recovery Asset Team (RAT), which specializes in freezing and recovering funds.
How to prevent check fraud
The following methods can help banks and businesses cut check fraud losses without slowing down legitimate deposits:
1. Install Positive Pay
Positive Pay allows banks to match checks presented for payment against a list of checks your business has issued.
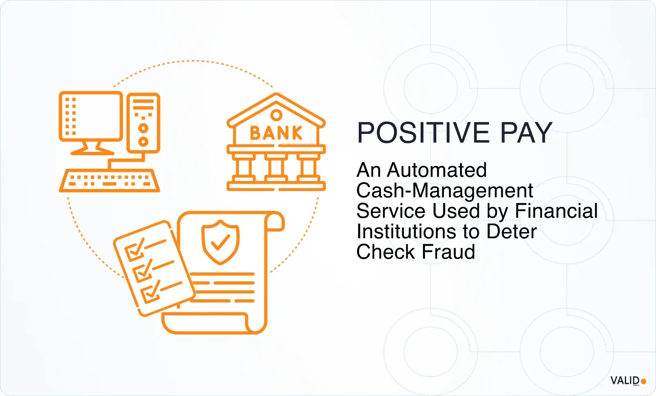
Adding Payee Positive Pay strengthens this control by verifying the payee line, making it harder for altered or counterfeit checks to slip through.
Steps to apply Positive Pay:
- Enroll in your bank's Positive Pay program and send issued check files daily.
- Include payee name details where available to catch alterations.
- Investigate and resolve flagged mismatches before the bank pays the items.
2. Detect counterfeits at the deposit
Stop counterfeit and altered checks at the point of presentment, not after posting. Image forensics and template analytics enable this.
Steps to detect counterfeits:
- Deploy image forensics to spot altered fields, template mismatches, or MICR anomalies.
- Integrate counterfeit detection into mobile capture and ATM systems.
- Train staff to escalate suspicious images during branch deposits.
Pro tip:
For real-time, high-accuracy intelligence on every check deposit, use CheckDetect. This solution identifies more than 75% of potential check deposit charge-offs with precision, allowing banks to apply efficient treatments at the point of presentment and transform deposit operations with actionable insights.
3. Use behavioral risk scoring across channels
Fraudsters often move checks through multiple deposit points, making behavioral analysis a powerful tool.
Steps to apply behavioral scoring:
- Monitor deposits across the branch, ATM, and mobile channels.
- Flag patterns, such as serial-number gaps, repeated channel hopping, or unusual cross-account activity.
- Utilize analytics platforms to identify anomalies in near real-time.
4. Apply dynamic holds
Rigid hold policies can frustrate customers, but dynamic holds enable banks to strike a balance between risk and a positive customer experience.
Steps to apply dynamic holds:
- Base holds on account tenure, deposit history, and check amount.
- Use Reg CC exception holds where risk is highest.
- Allow low-risk items to clear quickly to maintain trust and efficiency.
5. Educate customers on safe practices
Customer behavior is often the first line of defense. Businesses and individuals can reduce risk by modifying their check handling procedures.
Steps for education:
- Advise clients to avoid mailing checks in blue USPS collection boxes.
- Highlight the risk of stolen arrow keys that criminals use to raid mailboxes.
- Encourage secure drop-offs or digital payment alternatives where possible.
How VALID Systems prevents wire and check fraud in real time
Wire fraud and check fraud each pose distinct threats to banks, and understanding both is vital for robust risk management.
Wires demand speed and vigilance, and checks require visibility and analysis.
VALID Systems delivers precisely that. Here's how:
- Real-time decisioning for checks: With CheckDetect, banks can instantly score every deposited item before it clears. The system identifies the riskiest checks, including altered, counterfeit, or washed items, allowing fraud teams to hold those that require review while releasing the rest without delay.
- Continuous monitoring for wires: VALID applies behavioral analytics and corridor scoring to outbound wires. By analyzing beneficiary history, timing, and novelty, VALID highlights the few wires that carry real risk, allowing banks to review them without slowing the flow of legitimate payments.
- Behavioral and consortium intelligence: VALID doesn't just look at a transaction in isolation. Its scoring blends customer behavior, cross-bank consortium signals, and real-time analytics to identify anomalies that static rule sets miss.
- Operational insights: Beyond scoring, VALID equips banks with dashboards and reporting tools that reveal fraud trends and portfolio performance, turning raw detection into actionable intelligence.
The result: faster payments for customers, fewer losses for banks, and a stronger defense across both payment rails.
Looking to strengthen your fraud strategy?
Book a free consultation with VALID Systems and learn how real-time fraud scoring can help you stop high-risk wires and checks before they become unrecoverable losses.
